The master process can poll the status of its slave processes and keeps a list of known slaves. The resulting master-slave network may include a large number of hosts in widely different network locations. When a vulnerable host is found it is exploited and used to scan for other hosts with the same vulnerability or group of vulnerabilities. There are a number of steps that local network managers and network administrators can take to protect all of their own users as well as the rest of the Internet community: A "client puzzle" is a cryptographic problem that is generated in such a way as to be dependent upon time and information unique to the server and client request. 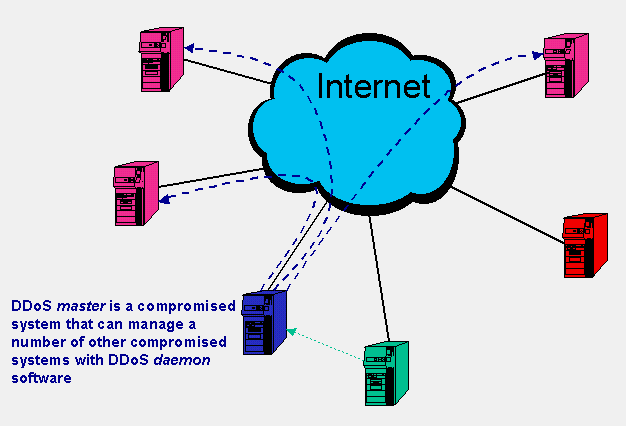
| Uploader: | Dairamar |
| Date Added: | 3 January 2008 |
| File Size: | 48.65 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 98677 |
| Price: | Free* [*Free Regsitration Required] |
In fact, techniques are typically employed to deliberately camouflage the identity and location of the master within the DDoS network.
Related Resources Store Articles Blogs. During their DDoS ttin00, Buy. Communication between the master and daemons can be obscured so that it becomes difficult to locate the master computer. If your systems have been compromised and attackers are running masters or slaves on your systems, you must take immediate action to fix the ddso holes that were used to compromise your system [2].
A single attacker may control several DoS master processes, giving instant access to huge numbers of slave processes.
Unauthorized Activity Detected
The trinoo or trin00 is a set of computer programs to conduct a DDoS attack. It is believed that trinoo networks have been set up on thousands of systems on the Internet that have been compromised by remote buffer overrun exploits.
DDoS attacks will be with us for some time but there are ways today to minimize them -- but they require continued diligence at locking down all of the hosts connected to the Internet. The hardware is defensive in nature at the receiving side.
DDOS Trin00 MasterDaemon Default PW
While both of these proposals requires a change to tens of thousands of routers in the Internet, it is a solution that can be gradually implemented, is backward compatible, and results in no negative affect to users. Once again Stacheldraht's attack model is the same as TFN and Trin00, but the communication between devices is different.
These programs are not viruses but DoS tools.
In the case of Trinoo there does not seem to be a limit to the number of daemon agents that one master server can control. As network security is once again threatened, Trend Micro faces this challenge by providing its customers with Scan DDoS, a free tool that detects the presence of hacker agents within a Unix or Linux environment.
The idea is that a bona fide client will only experience a modest delay getting trij00 connection during an attack, while the attacker will require an incredible amount of processing power to sustain the number of requests necessary for a noticeable interruption in service, quickly blocking the attack in effect, a reverse DoS.
ddps

The tools listed here are the best known, and most widely sued, but they are not the only ones and more tools are becoming available. This page was last edited on 23 Aprilat cdos These techniques make it difficult to analyze an attack while in progress and also to block attacking traffic and trace it back to its source. Rather trni00 receiving, for example, a thousand gigantic Pings per second from trin0 attacking site, the victim might receive one Ping per second from attacking sites. The hardware, of course, needs to somehow be informed about traffic level changes that are due to "normal" events, such as a new Super Bowl commercial being posted at the Ad Critic Web site or a new fashion show at Victoria Secret's Web site.
By using this site, you agree to the Terms of Use and Privacy Policy.
Unauthorized Request Blocked
Instead, the attacker launches the attack from the handlers. Ddox heavy DoS attacks have been described [1,2]. To use this tool, decompress and run script scanddos with directories or specified files to locate hacker agents. If you are the target of a large distributed DoS attack, there are no good ways to defend yourself. According to book seller Amazon.

The first set of vulnerable hosts are called handlers. The first well-publicized DDoS attack in the public press was in February The user's firewall has historically been used to protect the user from attacks from the outside world.
Trinoo also known as trin00, is a hacker agent that communicates primarily using TCP connections although trun00 is some indication that it was originally used solely for UDP connections.
Trinoo - Wikipedia
The file is self replicating and is modified on a regular basis as long as port 80 is active. These attacks are known as Distributed Denial of Service Attacks.
Any DoS defense that is based upon monitoring the volume of packets coming from a single address or single network will then fail since the attacks come from all over.
Check for the latest database updates First check if your F-Secure security program is using the latest detection database updatesthen try scanning the file again.
Slave processes can be installed on virtually any suitable system, as the hrin00 of a single slave process has very little effect on the overall performance of the network.

No comments:
Post a Comment